Download a PDF version of this Tip Sheet.
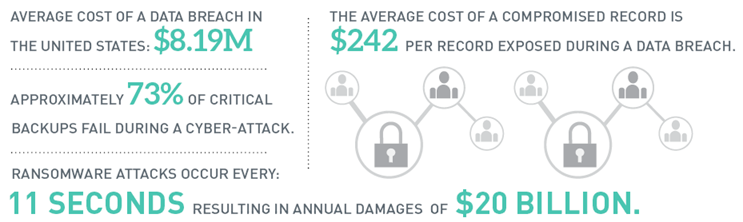
The average cost of a data breach today in the United States is ~8.19 Million USD. Ransomware attacks occur every 14 seconds and every 11 seconds by 2021. Approximately 73% of critical backups fail during a cyber-attack. The average cost of a compromised record is $242 per record exposed during a data breach. New data privacy laws enacted such as GDPR, CCPA and the NY-SHIELD act are levying substantial penalties to organizations that are not cyber fit. It is important to note that a company need not reside in Europe, California, or New York, for example, to be held accountable for data privacy violations.
It is a misconception to think data breaches occur only to collect a ransom. Modern cyber-attacks are often after more than just a ransom. Although training may help reduce the number of users who fall victim to phishing attempts, it is certainly not the fix. Consider that if a single user alone falls victim to a phishing email, the entire organization can be impacted. That single user need not be an IT Administrator with domain admin or superuser credentials for the entire environment and/or for critical business assets to be compromised.
Cyber intrusions are about the confidentiality, availability and integrity of the systems and data. Modern cyber threats to business are external hackers and even an internal threat actor, as well as government and legal actions in the form of violations and sanctions. In terms of internal threat actors, an independent poll was conducted during COVID-19 that found that ~57% of employees felt that they could engage in nefarious activities against the company they work for and get away with it, simply because they were working from home. Businesses must understand that during COVID-19 and the New Norm, that your organization’s attack surface has significantly expanded, especially with a distributed workforce and technology. Don’t wait until an incident occurs. For additional information about Withum’s cybersecurity services, contact our experts now.
Cloud does not automatically equate to better security. Cloud is simply someone else’s computer. Merely because your cloud provider is secure, does not make your company secure. If you are being told differently, ask your cloud provider to assume all liability on behalf of your company in the event that system and/or data is compromised on their impenetrable cloud. Mic drop.
Next-generation cyber-attacks are here now, and they are not science fiction either. They are called cyber kinetic attacks. These types of attacks cause physical damage to environments. So, regardless of whether backups are ‘good’, cyber kinetic attacks can brick environments. Thus, rendering physical, electronic equipment and data useless like a physical brick. Secure your environment via independent third-party audits.
Additional considerations should be adopted:
- Apply Security Controls and Filtering w/Artificial Intelligence Integration
- Virtual Tripwires (Identifies Anomalies in the Environment) Implement Self-Healing Smart Backups (Backups are typically poisoned by intruders)
- Conduct a 3rd Party Threat Emulation aka authorized hacking of environment, Business Continuity and Security Gap Assessment to verify the business’s confidentiality, availability, and integrity.
- 24/7/365 Independent 3rd Party Monitoring and validation of environments to provide a constant ‘checks-and-balance’ against people, processes, and technologies. This assures internal and external policy, data privacy and compliance adherence.



